Device Identity
Device Identity, part of Layer 1, provides an identity for robot clusters and services to integrate those identities into a cloud based IAM system.
The following components are part of the whole setup:
- Cloud:
IAM: Cloud Identity and Access ManagementKubernetes configmaps: used as a Key Management ServiceToken Vendor: token exchange service for OAuth2 service accountsrobot service-account: a GCP IAM service account that has the union of permissions that applications running on the robot cluster require
- Robot cluster (on-prem or edge):
Metadata Server: provides default credentials + project metadataSetup: special app used to register the workcell<App>: any app accessing the cloud
The following chapters explain the flows in more detail. Further information about the Token Vendor can be found in its docs
Setup
The setup flow is used to register a new robot cluster to a cloud project.
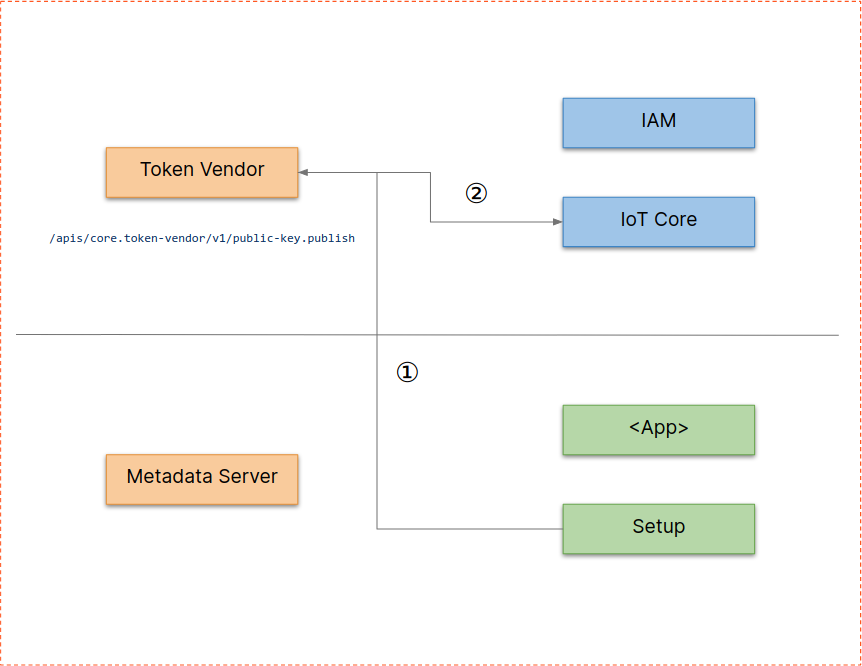
- (1) (Admin-)user runs
Setup, which generates a RSA key-pair and stores it as a K8S secret - (2)
Setupuploads the public key toToken Vendor - (3)
Token Vendorstores key inKubernetes
Authentication
The authentication flow is used to transparently make cloud API calls work for on-prem robot clusters.
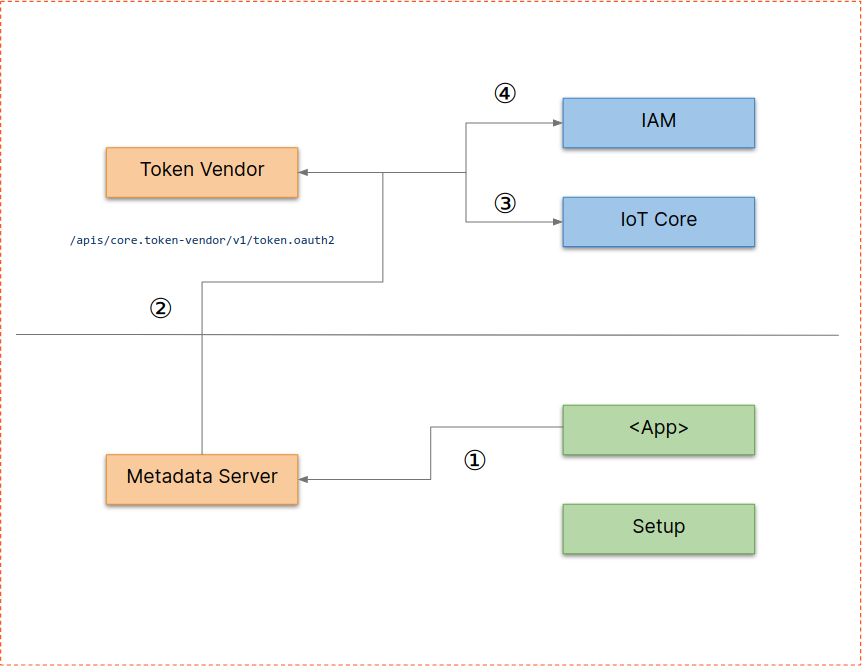
<App>creates an API client without loading any custom key material- (1) API client library probes
Metadata Serverto get ADCs (Application Default Credentials) - (2)
Metadata Servertalks toToken Vendorget an Access Token for therobot service-account - (3)
Token Vendorverifies the key the request has been signed with against the device registry - (4)
Token Vendorgets an Access Token for therobot service-accountfromIAM Token Vendorreturns Access Token throughMetadata Serverto the<App>and that can use it to call Cloud APIs under the scope of therobot service-account